Lab Overview
Continuing from last lab, the purpose of this lab is deploying certificates and activating key recovery as if a key becomes lost, that data that has been previously encrypted will be completely cut off and inaccessible. So in this lab, we will be going through restoring keys from archives and other methods
This lab will be using RT-LAN, WIN2016-DC and WIN10-WS and follows the CompTIA Security+ Certification (SYO -501) official guide which includes four exercises for lab eight.

Exercise One – Key Recovery Agent
The purpose of key recovering agents is when a key is created, that key is then encrypted by the agents public key and stored, so if whatever reason, the key can then be decrypted with the agents private key. The only issue with this, is that agents can not encrypt old keys that existed before the creation of the agent, so an agent should always be the first thing to be setup. So with a small understanding on what a KRC is, time to start up the WIN2016-DC system to implement it. Creating a new KRC is quite simple. Once the system is running and Certification Authority manager has been opened, all that is needed is to right click -> new template -> KRC. With the template set up, now lets request a certificate.
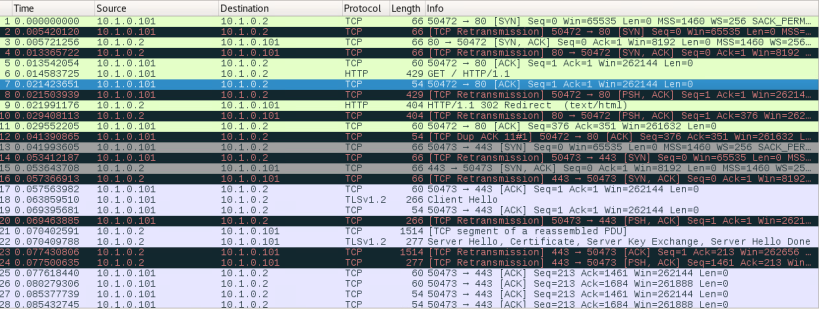
Switching over the the WIN10-WS system, we are able to request a trusted certificate via the https port, while this isn’t a standard way of doing it and shouldn’t be done in real world environment, for a lab it is fine. From here, we are able to locate the certificate server by entering in “WIN2016-DC.classroom.local/certsrv” or “10.1.0.1/certsrv”. however, upon doing this, we are greeted with a page that does not follow the lab.
After further researching, the lab was actually missleading, it states that the student should switch to the WIN10-WS system, however they shouldn’t. So after repeating the “10.1.0.1/certsrv” on the WIN2016-DC system, we get the correct page.
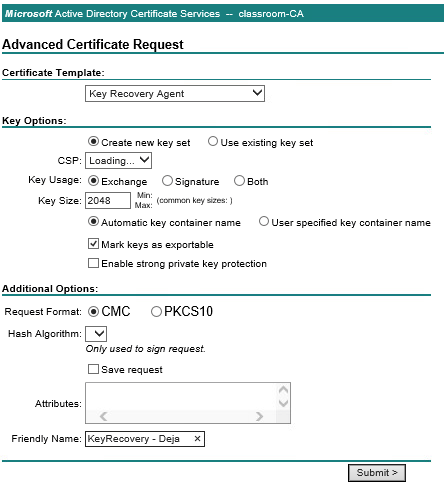
As i am currently not following the lab exactly, certain things have been changed.
- As the server requested the certificate it was instantly issued and became active
- WIN10-WS does not see any pending certificates as they didn’t request it
- WIN10-WS has to download new certificate
Now to configure the certificate server with details of the new recovery agent. Staying on WIN2016-DC, with the certificate server manager open. right click on classroom-CA -> properties -> recovery agents. Which ended in another failure, as the certificate was not there, so I decided to see if WIN07-WS could send the certificate request and I fond the issue, the certificate is communicating on HTTP not HTTPS. So i updated the port bindings for the webserver and tried again, using the WIN07-WS.
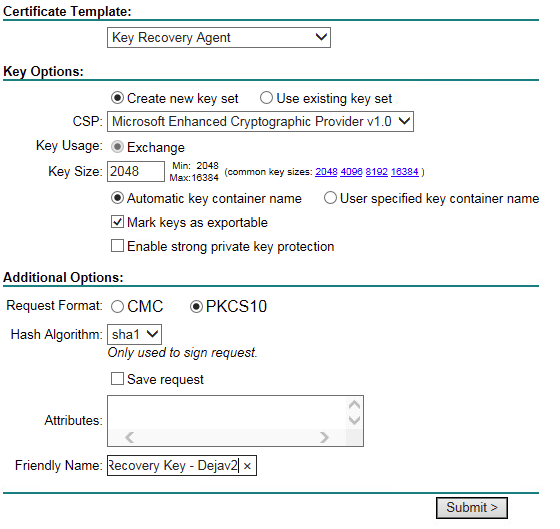
This time it looks more promising as it was able to load both CSP and Hash algorithm, compared to last time.

Now I can issue the certificate and install that follows the lab. Fast forward back to the recovery agent, i am now able to select the Key Recovery Agent, click OK and done!

Issues found:
(1) HTTPS port was not set up for the web server that was hosting the certificate server, making it insecure and not allowing certificate requests to be sent
(2) WIN10-WS has some settings set up incorrectly so it is unable to send a request, however WIN07-WS does
Exercise Two – User Certificates
Within a real world environment, a company can have a range from 10 users all the way up to 1,000’s of users, so manually approving each certificate like we did in the last exercise is bad practice, so how can we automatic it, while still making sure only valid users can access them. This can be done through group policies or through certification template list exercise one.
Option One – Auto Enroll via Group Policy Management
Once we have located and opened up the GPO, in this case its “classroom Domain Policy”, navigate to public key policies which is under security settings, from here their is a setting for “auto-enrollment” enable this policy and its done, all future certificate requests will be auto accepted if the user is part of that GPO.
Option Two – Auto Enroll via Certificate Template
Just like exercise one, we are able to create a new template, under the certificate server manager, however in this case we will be just duplicating and existing on. For this example, I will use the user template. From here, we can change all sorts of different components for how the this template will interact, however for this exercise we just need to auto enrollment. Auto enrollment can be found under the security tab, just select the user group and tick auto enroll.
Exercise Three – Encrypting File System
Within windows business editions, we are able to encrypt files by using File Encryption Keys which uses the symmetric key algorithm. Below is a simple diagram of how it works, which was by Soumyasch – Derived from EFS operation scheme.png. Originally by User: Wagner51, CC BY-SA 3.0.

For this exercise I will be starting off in the WIN10-WS system and ill be using an example user, called “Sam”. After logging in successfully, I have created example files to be encrypted by EFS. From here i am apply to apply encryption by accessing the advance settings of properties. now the files are highlighted with green text and got a padlock overlay on them

Exercise Question – What are the certificate thumbprints?
Sam: CF25 D34B E372 6788 8FAC 3E3E BB00 2D52 B3CD AFC4
Admin: FED8 C0DF 3005 71D7 44B7 E0A0 0A34 DFC4 18CC 5CBA
so now what will happen if we delete the private key to access those files? firstly it would be good to back up the private key in a exported file before deletion. We are able to do this via Microsoft’s Management Console. Within this console we able able to locate certificates and from here right click -> export and following the export wizard should successfully export the certificate key that was used to encrypt the files. now we are able to delete the certificate safety. With the certificate gone, I get this result when trying to access the files

Exercise Four – Key Recovery
So how can we recovery the key if for some reason the export has been deleted or misplaced. Only users with administrative permissions and access to the server are able to recovery keys. On the WIN2016-DC we are able to see issued certificates and because of the current set up, once Sam deleted their certificate, they were instantly auto-enrolled with a new one and thus new keys.
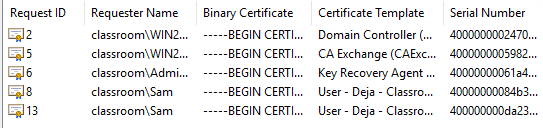
From here, we are able to select the deleted key (Request ID – 8), find the serial number and via command line, request the private key by “certutil – getkey “serialnumber”. request ID -8’s serial number has been highlighted.

From this command, it has exported a blob of information. So now if we switch to the clients system(WIN07-WS) while in administrator, we can recover the key, by using that blob with another certutil command line

Now if we sign in, using sams account, we can view currently using certificates, lets see if using the recover had work. after opening up the certificate console via the MMC, we can see that one certificate is issued to sam, however, as we noted above, this was a new one (requestID-13), not the old one, so the files will still be locked of, so go ahead and delete it
This is because while we unloaded it from the blob located in the server under the name “recovered”, we haven’t imported it, so after following the import wizard, the certificate should be reapplied to the account!